
Ransomware Attacks
Ransomware is the biggest money maker for cybercriminals in current day and age. According to the latest report by European authorities, Ransomware Attacks has impacted over 10,000 organisations and 200,000 individuals in over 150 countries. These cyber-attacks are real threats to any business including small & medium size companies (SMBs).
Many SMB enterprises think that they are too small for hackers to target. According to an Internet Security Threat Report by Symantec, almost 60% of all cyber-attacks target SMBs, and approximately 75% of all spear-phishing scams were directed at small companies. As they are totally unprepared towards these threats, the damages can be monumental and recovery path tough.
But let’s understand Ransomware first.
What is Ransomware?
Cybercriminals deploy Ransomware to infiltrate and encrypt files, or devices and networks. They demand payment for release of files or if payment is not made they threaten to steal the secure data. You will have heard about recent Ransomware Attacks that impacted more than 150 countries. According to an interview report of Assistant Minister for cyber-security Den Tehan – “Ransomware had not affected Australia’s critical infrastructure or Government agencies.” However, this should be considered a wakeup call.

ICTechnology Ransomware Attacks
Here, we have defined the top 6 ways Ransomware can attack your system or your network without even your knowledge.
-
Increased Use of Mobile Device: Now-a-days many service providers and third-party suppliers have become part of the mobile and IoT ecosystem. However, some of them may not have completed all security testing. Connecting to such devices can breach your device’s security.

ICTechnology Ransomware Attacks
- Spam: Simply put, spam is a junk email, everyone knows it. But imagine if your inbox is getting flooded with too many emails prompting you to download something from a link. This spam email can easily turn out to be a Ransomware attack on your system.

ICTechnology Ransomware Attacks
- Password Attacks: As the name suggests, a password attack is any third party trying to gain access to your system by cracking your security code or passwords. It doesn’t require any software to be downloaded or malicious code to run on a system. Attackers use many methods to access passwords.

- Phishing: Phishing is a technique to steal the sensitive information by sending a phishing link via email and prompting the user to click it. This link redirects the users to a dummy site that steals the data.

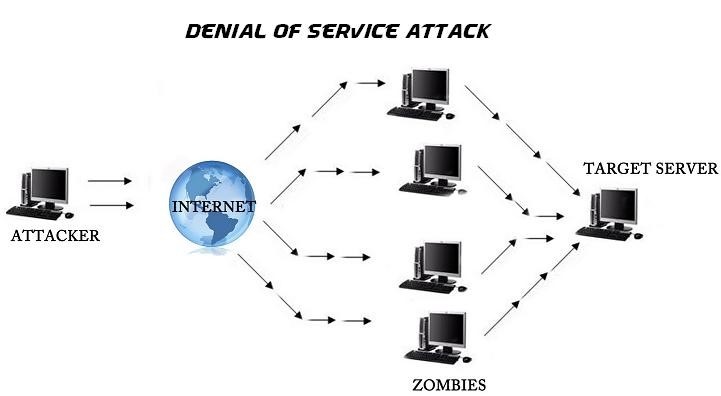
- Denial-of-Service (DoS) Attacks: A DoS attack targets to disrupt the service of a network. Cyber criminals send high volumes of data or traffic via network to block the network and stop functioning. Due to DOS attack, a victim may not even realise that his/her computer has been hijacked.
- Rogue Software: Rogue software are a type of malware that masquerades as legitimate. Cyber attacker or rogue software designer build pop-up windows to make it look legitimate. This alert asks the user to download some software to maintain security of your system. Whenever you agree to their terms and condition, they instantly downloaded on your system. Rogue software can corrupt all your important data or even devices.
Securing your sensitive data and protecting your network from cybercriminals should be an important part of our IT Management strategy. You can beat the cyber attacker with a clear plan to action of back-up and double-shield security for your systems. IT managed service providers can play a big role in rescuing your organisation from these unknown security breaches that can leave your business vulnerable.
ICTechnology offers secure solutions to improve your cybersecurity before any breach. With a streamlined execution process, ICTechnology follows real time intelligence tools and breach notification protocols to safeguard your sensitive data for the entire organisation. It will help you fight back these frequent attacks.
If you have any query about security threats or if you are looking for a secure solution for your business enterprise, please call us or drop your query. For more information please visit @ www.ictechnology.com.au





