In today’s highly dynamic work environment, Cloud Computing is a proven technology to make your business more efficient and thus, profitable. According to different researches and statistics numbers, incorporating Cloud technology to any business, big or small, results in high quality of services with the lowest expenses on operational needs.
27% of the larger organisations have already shifted their ERP to the Cloud and 78% are more likely to switch. However, small businesses are still stuck with old traditional systems and don’t want to move on. It can be due to multiple reasons. Let’s dig deeper into this issue:
Why SMBs should Partner with Managed Services Providers
Cybersecurity is one of the biggest concerns for businesses today. In this article we will elaborate Why SMBs should Partner with Managed Services Providers. Small and medium size companies try to follow their larger counterparts by adopting new skills to manage security but usually fall short because of several reasons. It can be due to the lack of infrastructure they currently have, the tools they deploy or the process they adopt to drive these services.
[caption id="attachment_419" align="aligncenter" width="801"]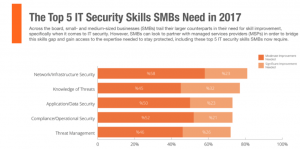 Why SMBs should Partner with Managed Services Providers[/caption]
Why SMBs should Partner with Managed Services Providers[/caption]
Check out these three major drawbacks that SMB’s face when trying to resolve IT issues on their own:
(1) Lack of Skills: Finding an expert who is proficient with the skills is always an on-going challenge in the business world – specifically when it comes to IT security. You may be amazed to know that close to 45% people are unaware of threats to their Cybersecurity. One reason could be lack of training, certification, or hands-on experience. Nevertheless, lack of skills has become one of the biggest obstacles to defend the business from unstoppable threats.
Security, Backup, Connectivity - 3 Pillars That Can Guard Your Business From Hackers.
Security, Backup, Connectivity - Three Pillars That Can Guard Your Business From Hackers. - Many of us are still trying to recover from the recent Ransomware ‘WannaCry’ attack that affected almost 150 countries and 4,00,000 machines across the globe. If you were one of the victims and are still contemplating a security and backup solution, you are stretching your luck too much.
According to computer security experts, the first thing you need to identify is - What are the key solutions that you need to implement for making your cyber security strong?






