Nowadays, we cannot even think of a day without technology. For a business operation point of view, technology is a lot more critical. The functional area of any business relies heavily on the IT infrastructure, i.e. Data storage, networks, hardware, software and so on. Therefore, entrepreneurs or business executives want to craft an effective strategic plan to be successful in every significant event.
4 Ways Good Managed Service Provider Can Grow Your Business Your business actually needs an expert hand! 4 Ways Good Managed Service Provider Can Grow Your Business Like Never Before - Probably you are not looking for a change right now and you are happy with the way things are with your IT. But can you keep up with your competitors and stay ahead without
IT directors, administrators, and CIOs managing enterprise set-ups, spanning multiple cities or countries need efficient and secure networks. It is true that larger organizations have more complex IT requirements compared to the small-to-medium businesses (SMB). However, this doesn’t mean that SMBs don’t need those set-ups. In most small companies or even 250 people, they may have one IT person in place of IT managed services to manage all network related issues around the office. You can imagine how efficient that would be especially keeping up with the changing technology or watching out for cyber-attacks.
Beyond Outsourcing. Lets Be A Managed Services Partner.
Beyond Just Outsourcing. Lets Be A Managed Services Partner - Tight budgets, limited resources! Are you facing a similar situation in your business? If yes, what’s your plan to drive your business forward and make it more profitable in current situation? When businesses are in growth cycles or experiencing a slowdown the top priority is how to manage budgets prudently so that it supports growth and scales the operations in a secure and reliable way.
One common approach for a people-centric company is to do a deep analysis of business operations that can help cut down overall expenses. Some tasks like IT network security, Cloud management businesses often require hiring expensive resources and block unnecessary funds. But sometimes businesses don’t want to outsource it. So, what’s the right path?
Top 5 Reasons Why SMBs Should Use IT Managed Services
Top 5 Reasons Why SMBs Should Use IT Managed Services - According to a popular research, 80% of companies including SMBs that adopt ‘Cloud Computing’ see improvements in their IT spend within six months. Another report by ‘Telsyte’ forecasts that the total market value for Public Cloud infrastructure services in Australia will reach up to $775 million by 2019 from $366 million in 2015.
These facts are a clear indication that SMBs can achieve lower operations cost by replacing their regular IT systems with public cloud offerings, even business in critical areas such as business intelligence, customer relationship management (CRM) or enterprise resource planning (ERP). Increased flexibility with Cloud computing allows SMB employees to be more mobile - both in and out of the workplace. This generates the need of expert managed service providers that can bring mobility to your organisation.
Let's take a deeper look into the top five drivers for hiring managed service providers (MSP):
Why SMBs should Partner with Managed Services Providers
Cybersecurity is one of the biggest concerns for businesses today. In this article we will elaborate Why SMBs should Partner with Managed Services Providers. Small and medium size companies try to follow their larger counterparts by adopting new skills to manage security but usually fall short because of several reasons. It can be due to the lack of infrastructure they currently have, the tools they deploy or the process they adopt to drive these services.
[caption id="attachment_419" align="aligncenter" width="801"]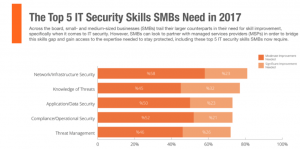 Why SMBs should Partner with Managed Services Providers[/caption]
Why SMBs should Partner with Managed Services Providers[/caption]
Check out these three major drawbacks that SMB’s face when trying to resolve IT issues on their own:
(1) Lack of Skills: Finding an expert who is proficient with the skills is always an on-going challenge in the business world – specifically when it comes to IT security. You may be amazed to know that close to 45% people are unaware of threats to their Cybersecurity. One reason could be lack of training, certification, or hands-on experience. Nevertheless, lack of skills has become one of the biggest obstacles to defend the business from unstoppable threats.









